CIA Triad: What It Is and How to Apply It in Cybersecurity

Cybersecurity is increasingly gaining prominence in organizations, whether due to the imminent threat of cyberattacks or the commitment to safeguarding customer and partner information. The fact is that many companies are already unknowingly adhering to the principles of the CIA Triad.
However, there are still organizations that feel somewhat lost regarding how and when to implement cybersecurity measures in their operations. In this context, the CIA Triad provides guidance on which aspects should be considered when striving to keep businesses secure through its three security principles.
Are you familiar with the principles that underpin the CIA Triad? If not, continue reading this article to learn how this concept can make your business safer. Enjoy your reading!
What is the CIA Triad? The CIA Triad is an essential concept for companies to protect themselves against cybercrime, guiding the implementation of security policies and best practices in digital environments.
Moreover, the CIA Triad is founded on three principles: confidentiality, integrity, and availability. It's important to note that these principles are interdependent, and effectively balancing them is crucial for protecting information against cyber threats and ensuring that operations remain secure and reliable.
Thus, the lack of such measures can make a company more susceptible to cybersecurity incidents, potentially leading to operational damage and reputational harm.
What are the principles of the CIA Triad and how can they be applied? The principles of the CIA Triad, when applied in an integrated manner, form a solid foundation for effective security strategies that ensure comprehensive protection of information and information systems.
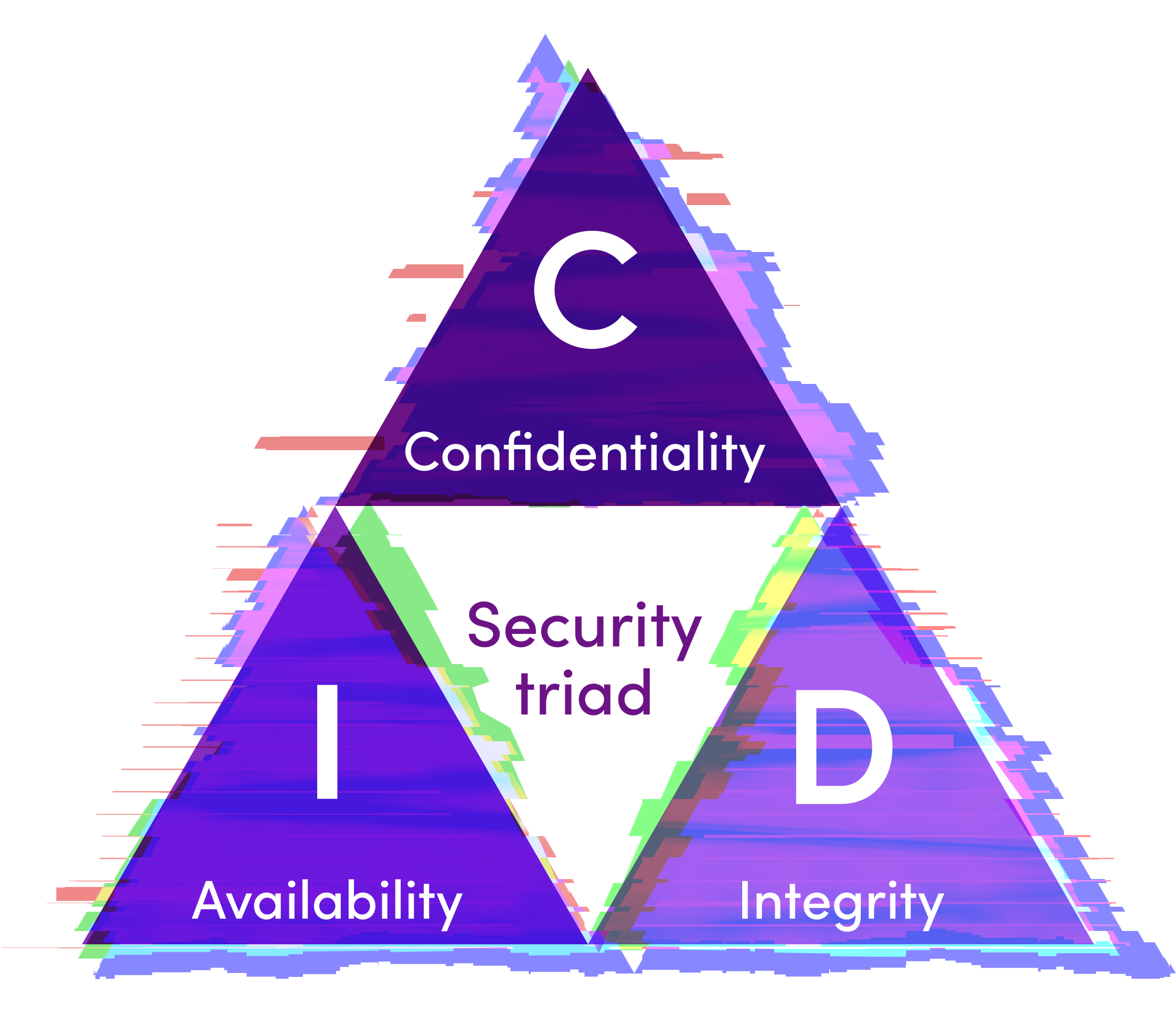
Understand what each of these pillars represents and how they can be applied in cybersecurity:
Confidentiality
Confidentiality is the principle aimed at preserving digital privacy and the sensitivity of information. To achieve this goal, access control practices are implemented to ensure that only authorized users can access certain information.
Additionally, encryption plays a crucial role in protecting confidential data during storage and transmission, transforming information into an unreadable format to prevent unauthorized access.
Integrity
Integrity focuses on maintaining the accuracy and consistency of information over time. To ensure data integrity, security techniques such as checksums and hash functions are used. These measures generate unique values for datasets, allowing any accidental or malicious changes to be detected.
Version control practices are also commonly applied to track and manage changes in documents and systems, thus preventing improper manipulation of information.
Availability
Availability refers to the ability to keep information resources accessible when needed. Redundancy strategies, such as server replication and the use of backup systems, are adopted to mitigate failures and ensure that services remain available even in the face of unexpected events.
Disaster recovery plans can be developed to handle critical situations, allowing for the rapid restoration of systems and data after incidents that may affect availability.
Why apply the CIA Triad in cybersecurity?
As you’ve seen throughout this article, applying the CIA Triad in cybersecurity is essential because it provides a solid framework for protecting information and systems against digital threats.
Here are some reasons why this approach is crucial for businesses:
- Comprehensive Protection: The CIA Triad addresses three essential aspects of information security, ensuring that protection is more comprehensive. It doesn’t just focus on preventing unauthorized access, but also on maintaining data integrity and ensuring continuous system availability.
- Compliance with Regulations: Many security regulations and standards, such as LGPD, incorporate the principles of the CIA Triad. Therefore, adopting this approach helps organizations meet compliance requirements more easily.
- Protection Against Threats: By balancing confidentiality, integrity, and availability, the CIA Triad aids in protecting against a variety of threats, including cyberattacks, data breaches, information manipulation, and service interruptions.
- Risk Management: Understanding and applying the principles of the CIA Triad allows organizations to manage risks more effectively. Identifying and mitigating risks related to confidentiality, integrity, and availability is crucial for maintaining security in a dynamic digital environment.
- Positive Reputation: A violation of any principle can have serious consequences for an organization’s reputation. Consistent application of the CIA Triad demonstrates a serious commitment to security and can strengthen trust with customers and partners.
- Adaptation to New Threats: The landscape of cyber threats is constantly evolving. In this context, the CIA Triad provides a flexible framework that can be adapted to address new threats as they arise, making it a resilient foundation for security strategies.
Did you enjoy learning how the CIA Triad helps keep companies safer against cyber threats? Access more related content on the BugHunt blog or follow us on our social media.

