Bug Bounty and the paradox of security
Cyclic testing is increasingly important for information security. When a system is developed and tested, it is based on the security knowledge available at that time. Therefore, adopting a persistent and cyclical strategy for your testing is essential.

A paradox in the security field stems from the phrase "a system is never secure," and this text reflects on it.
This maxim can lead to two extreme (illustrative) behaviors: either "over-security," which is an exaggerated emphasis on addressing security aspects, resulting in high financial costs, time, or even the non-launch of the project; or, on the other extreme, the approach of postponing, i.e., responding to security incidents as they occur during operation.
In real life, companies are working with best practices and recommendations for secure development— and, where applicable, sector-specific regulations. According to a Veracode study [1], a significant portion of security efforts has been invested during development (programming). It also shows the reality where these efforts compete with challenges such as:
- Meeting internal audit processes;
- Meeting project deadlines and budget;
- Fulfilling client and/or regulatory requirements.
The study [1] further notes that the methods used for secure development include:
- Web Application Firewall
- Runtime protection
- Penetration testing
- Static code analysis
- Dynamic analysis
- Interactive testing
Returning to the initial phrase—“a system is never secure”—the security efforts made during development are essential but do not address an important aspect of security: the temporal aspect. That is, when a system is developed and tested, it is based on the security knowledge available at that moment, and as common sense in security suggests, vulnerabilities and tools emerge daily. A complicating factor is that all vulnerabilities must be resolved by the developer, while the adversary needs only one breach.
To illustrate this issue, we have the case of the Heartbleed vulnerability, disclosed in April 2014, which allowed attackers to read protected memory remotely due to a flaw in OpenSSL. According to [2], after the vulnerability was disclosed, there was a significant increase in scans for vulnerable systems 22 hours after the vulnerability release, as shown in the figure below. The authors state that no events were observed before April 8, 2014.
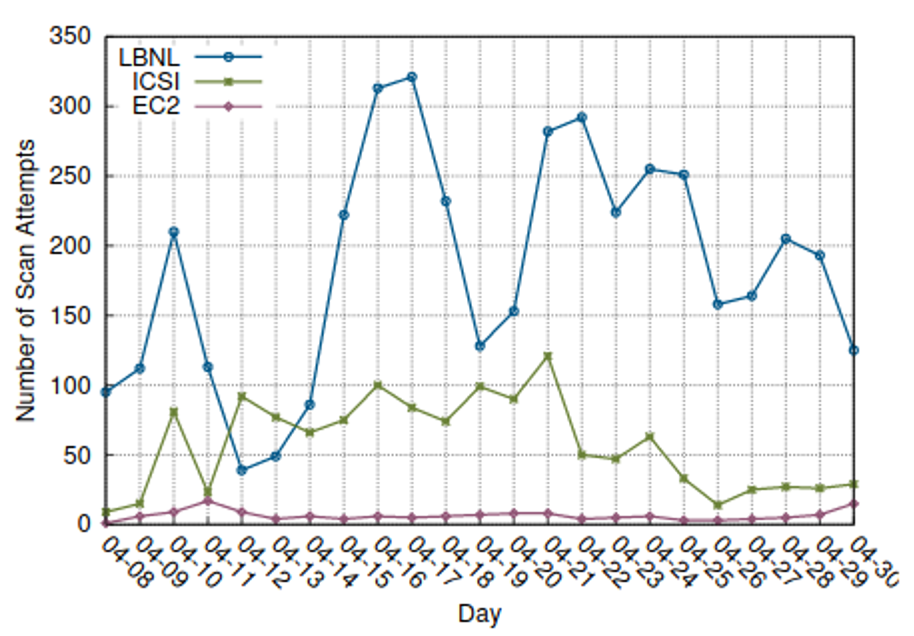
The authors also state that there was a significant effort to patch systems in the first two weeks after the vulnerability disclosure, but this effort stabilized over time, with 3% of HTTPS sites in the Alexa Top 1 Million still vulnerable two months later.
To address security during operation with continuous security assessments, or to include experts with complementary knowledge to your development processes, there are bug bounty programs.
BugHunt is the first Brazilian bug bounty platform and offers tailored programs to meet the needs of various businesses.
Feel free to contact us to learn more.

